pfSense + OpenVPN autenticando no Active Directory
pfSense + OpenVPN autenticando no Active Directory
Hello my Friends (TI) 🙂
Dando continuidade aos trabalhos hoje trago a vocês mais um tutorial sobre pfSense + OpenVPN que eu acredito que será muito útil para quem deseja aplicar as configurações de autenticação de sua VPN client to site através de Active Directory.
Para seguir a leitura deste tutorial recomendo que você primeiramente veja como configurar a Integração pfSense com Active Directory pois sem esta etapa você não irá conseguir entender e aplicar o tema aqui abordado.
Para iniciar a configuração do OpenVPN clique em VPN e selecione OpenVPN.
Agora iremos iniciar o Wizard do OpenVPN para realizar a primeira configuração.
Em nosso laboratório iremos configurar a autenticação dos usuários da VPN cliente to site através do LDAP, ou seja autenticando com usuários do Active Directory
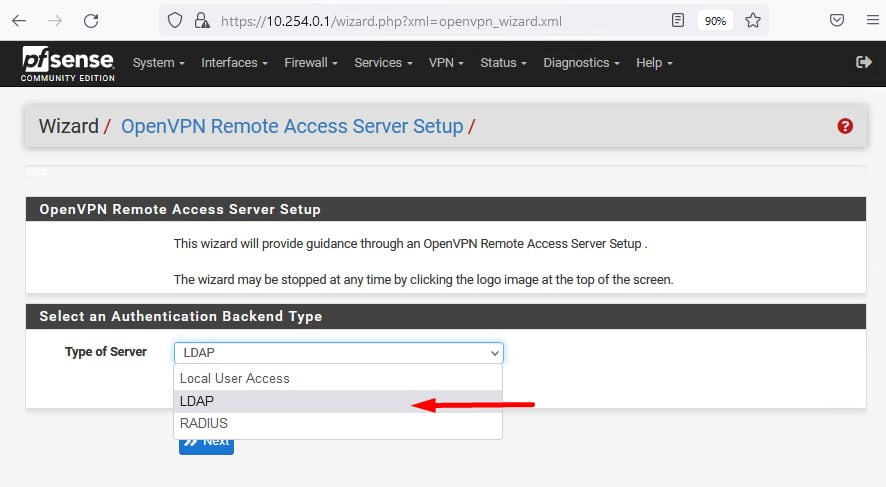
Após selecionada a opção LDAP e ter clicado em Next será apresentada o Step 1, como temos apenas uma configuração do Active Directory neste laboratório apenas o nome “AD” será apresentado, clique em Next.
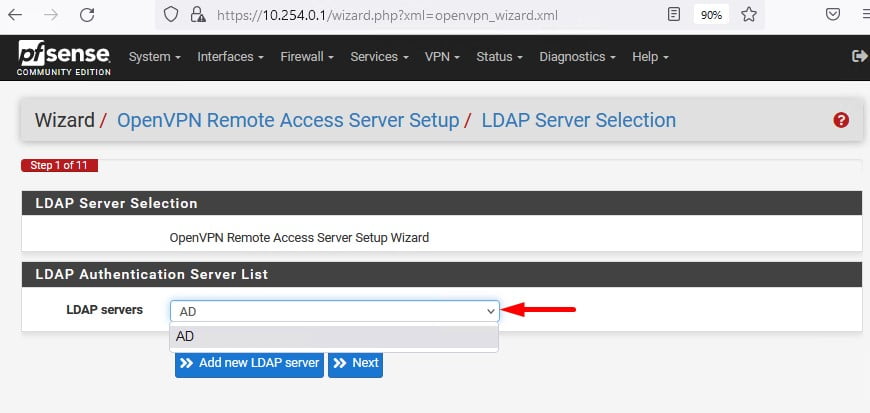
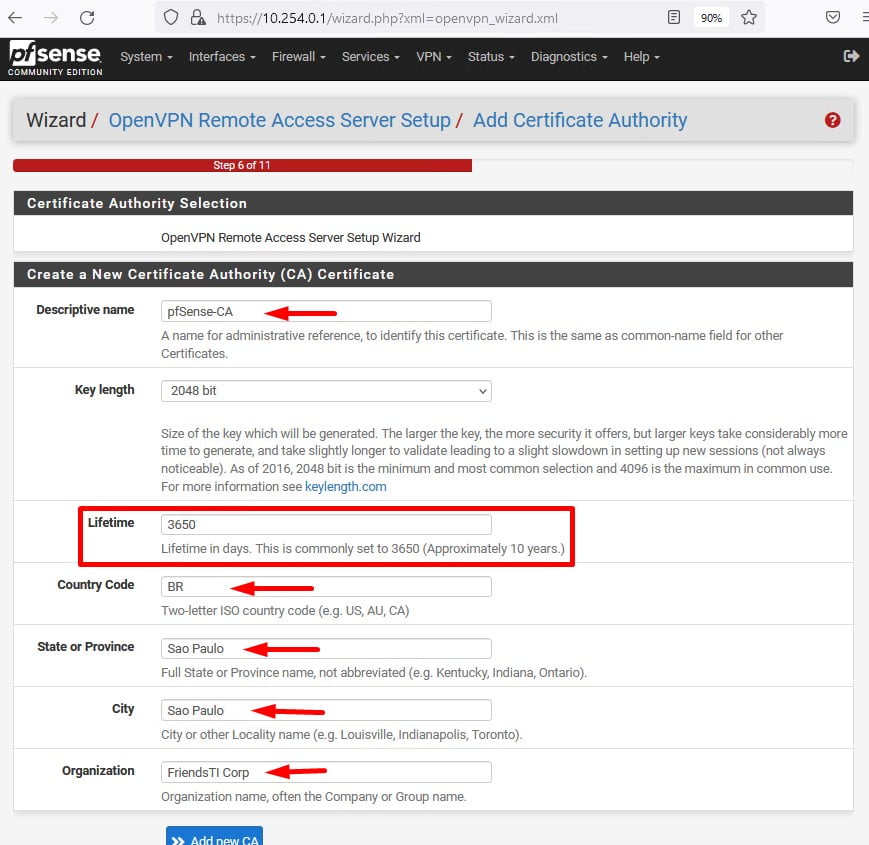
Seguindo o Wizard será necessário criar o Certificate Authority CA, preencha os campos conforme o print.
Descriptive name: pfSense-CA (Nome para Autoridade Certificadora)
Lifetime: 3650 (Neste cenário estamos utilizando 10 anos, porem você pode reduzir conforme sua necessidade)
Country Code: BR
State or Province: Sao Paulo
City: Sao Paulo
Organization: Friends Corp
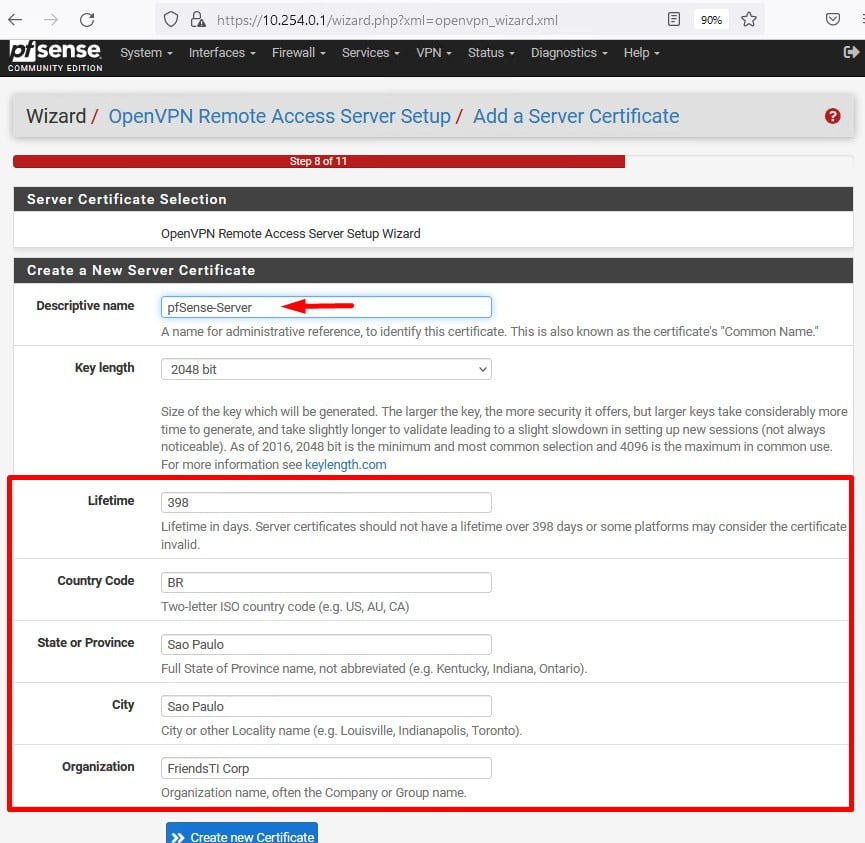
Na próxima tela possivelmente será necessário preencher apenas o Descriptive Name.
Em seguida selecione a interface que será utilizada, neste laboratório utilizamos a WAN porem você pode ter renomeado a interfaces de WAN ou até mesmo ter mais de uma.
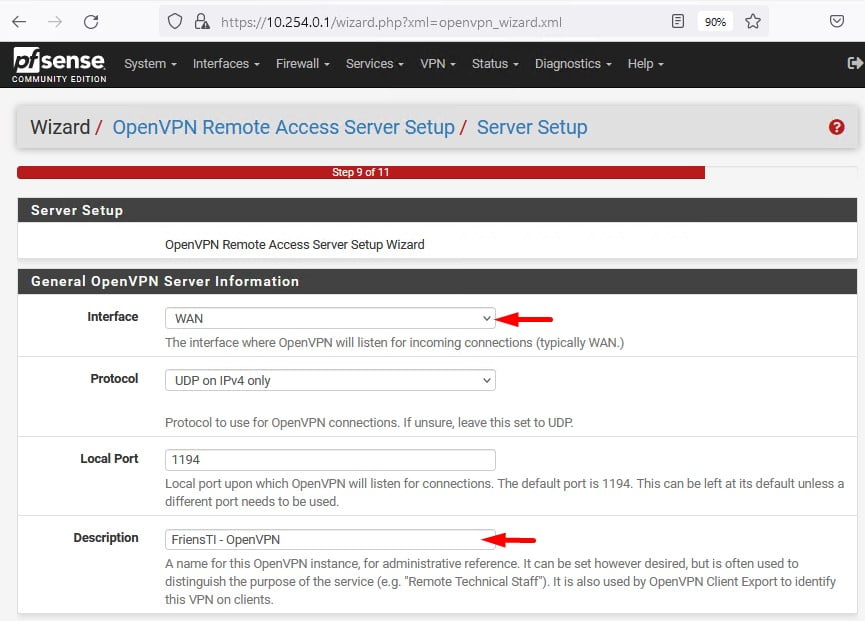
Desça a barra de rolagem até Tunnel Settings e conforme a sua necessidade preencha as configurações.
Tunnel Network: 172.16.0.0/24 (Para este tutorial utilizei outra rede privada pois meu pfSense está sobre um Hype-V)
Local Network: 10.254.0.0/24 (A rede LAN do meu pfSense)
As demais configurações não serão abordadas neste tutorial, porem você pode ler a respeito destas configurações na documentação oficial clicando aqui.
![c
Tunnel Settings
Redirect Gateway
Local Network
Allow Conwression
Compression
Type-of-service
Inter-Client
Comnwnication
Duplicate
Connections
O https://10.254.0.1
This is the virtual network used for private communications between this server and client hosts expressed using CIDR
notation (eg_ 10.0.8.0/24)_ The first network address will be assigned to the server virtual interface. The remaining network
addresses will be assigned to connecting clients.
Force all client generated traffic through the tunnel.
10.254.
This is the network that will be accessible from the remote endpoint, expressed as a CIDR range. This may be left blank if
not adding a route to the local network through this tunnel on the remote machine. This is generally set to the LAN network.
Specify the maximum number of clients allowed to concurrently connect to this server.
Refuse any non-stub compression (Most secure)
Allow compression to be used with this VPN instance, which is potentially insecure.
Disable Compression [Omit preference]
Compress tunnel packets using the chosen option. Can save bandwidth, but is potentially insecure and may expose data.
This setting has no effect if compression is not allowed. Adaptive compression will dynamically disable compression for a
period of time if OpenVPN detects that the data in the packets is not being compressed efficiently.
Set the TOS IP header value of tunnel packets to match the encapsulated packets TOS value.
Allow communication beü•een clients connected to this server.
Allow multiple concurrent connections from clients using the same Common Name.
NOTE: This is not generally recommended, but may be needed for some scenarios.](https://friendsti.com.br/wp-content/uploads/image-19.jpeg)
Como estamos utilizando um Active directory podemos também configurar o DNS de sua LAN, preencha as configurações conforme o print e em seguida clique em Next.
DNS Default Domain: friendsti.com.br (Seu dominio local, no meu caso friendsti.com.br)
DNS Server 1: 10.254.0.10 (O IP do servidor de Active Directory que também é o DNS local)
DNS Server 2: 8.8.8.8 (fica a seu critério configurar um segundo DNS local ou até mesmo um público como neste caso)
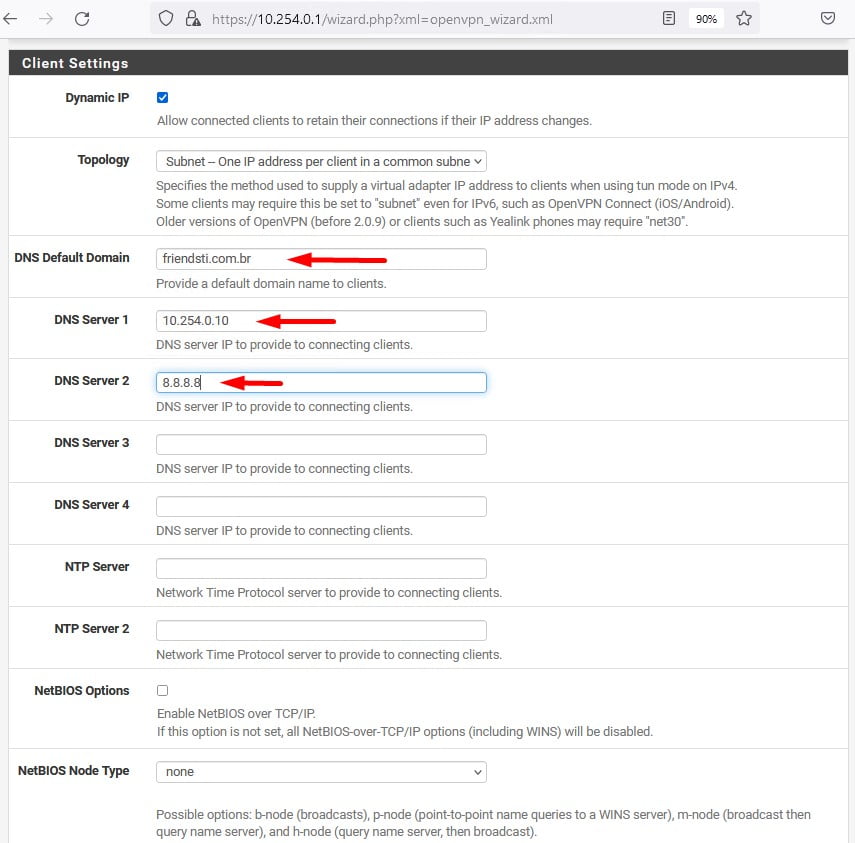
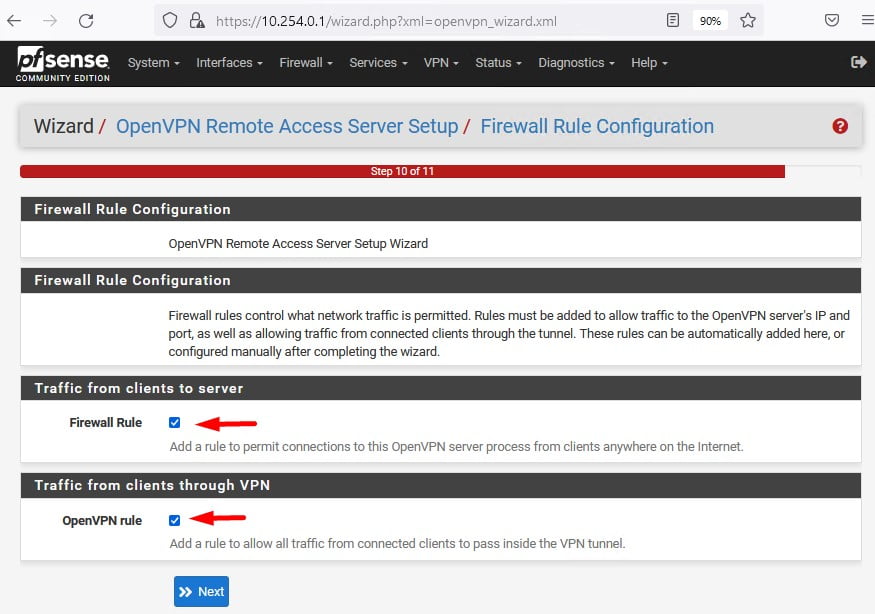
Na última configuração deste Wizard recomendo que você selecione Firewall Rule e OpenVPN Rule para que sejam criadas as regras de firewall de forma automática nas interfaces.
Pronto o Wizard da configuração do OpenVPN foi concluído, clique em Finish
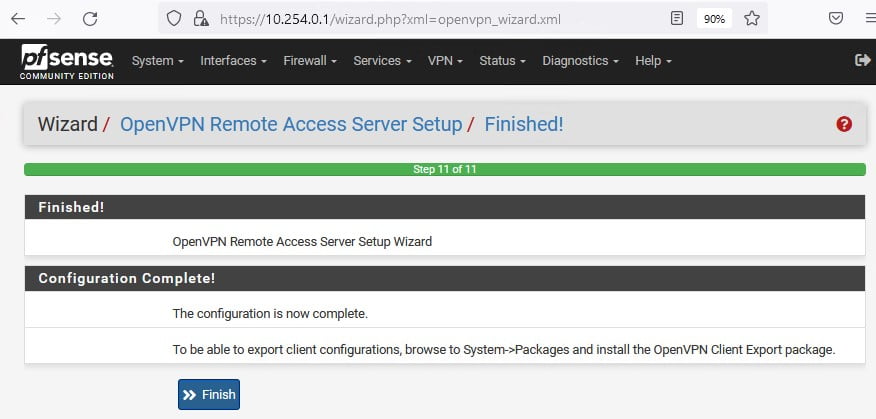
As configurações ainda não acabaram, fique atento aos próximos passos que são muito importantes para que você possa utilizar o pfSense + OpenVPN para autenticar através do Active Directory.
Observe no print a seguir, que é a tela após finish do wizard, que o modo de autenticação é apenas o User Auth ou seja está sua VPN será autenticada apenas com usuário e senha, vamos editar e configurar para que possamos utilizar autenticação através de certificado SSL/TLS e o usuário e senha do seu Active Directory.
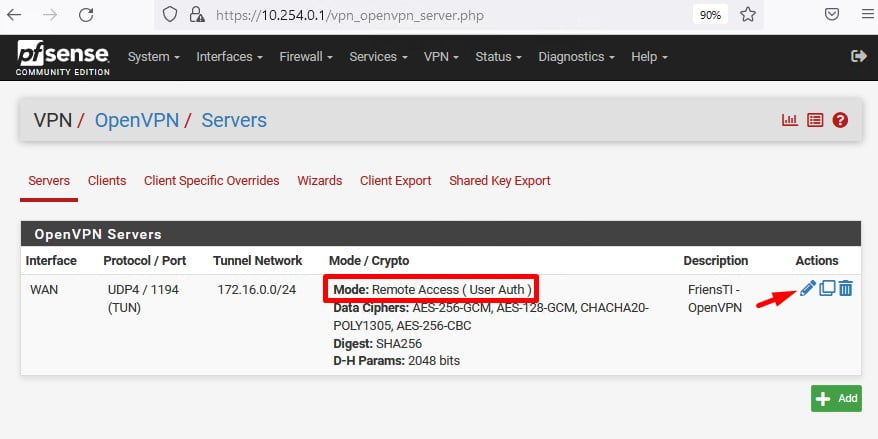
Na configuração Server Mode altere para Remote Access ( SSL/TLS + User Auth ) e clique em salvar.
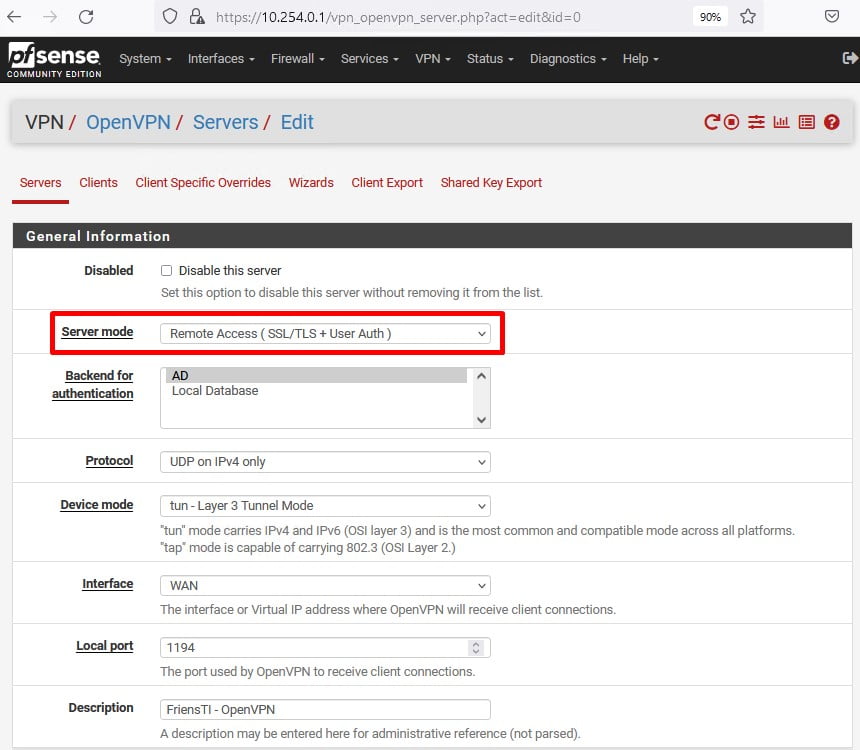
Após aplicado a configuração anterior agora iremos criar o certificado para o usuário que utilizará a VPN, acesse a aba System e clique em Cetificate Manager.
Agora clique em Certificates e depois em “Add”, Preencha o campo Descriptive Name e Common Name exatamante com o sAMAccountName do usuário em seguida clique em Salvar.
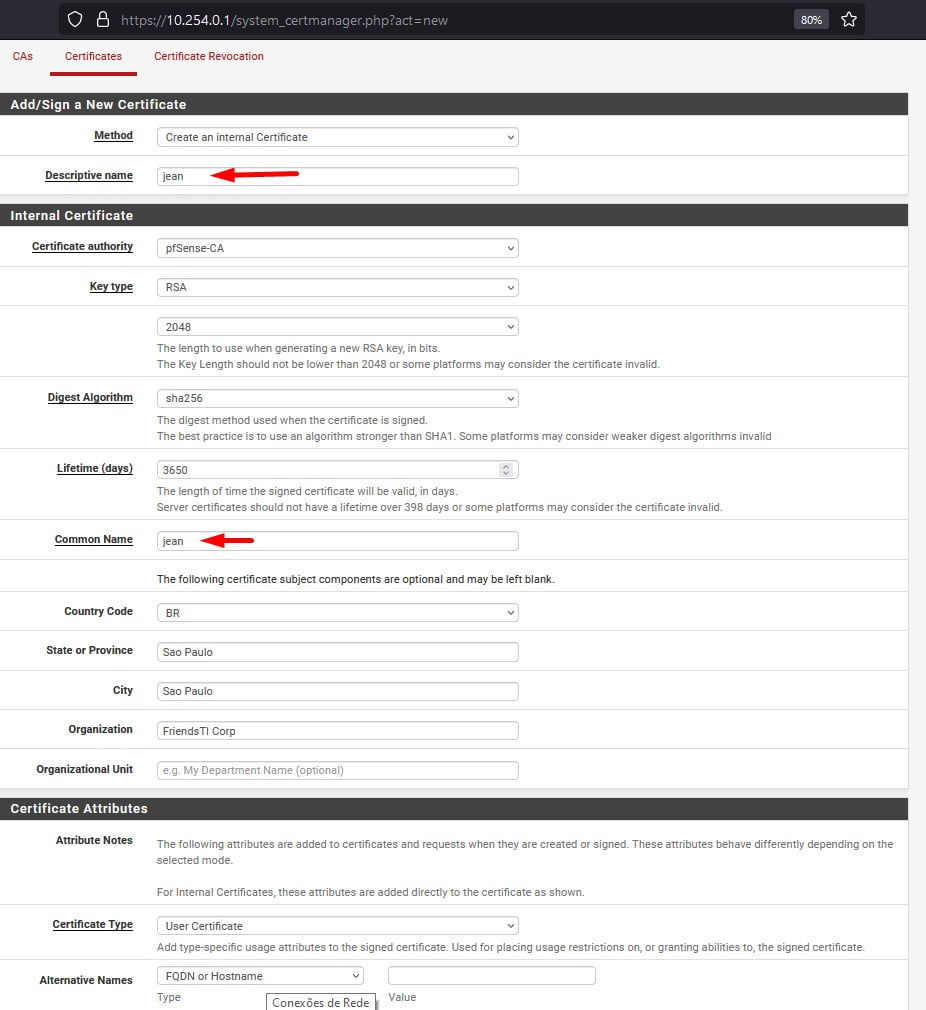
Nesta próxima etapa será necessário exportar as configurações do usuário, configurações do OpenVPN e o certificado do usuário.
Para isso podemos instalar um pacote chamado OpenVPN Client Export, clique na aba System em seguida Package Manager e localize a opção Available Packages.
No campo Search Term digite “openvpn” e você deve ter um resultado parecido com o deste print abaixo, clique em install no pacote openvpn-client-export e aguarde até a conclusão.
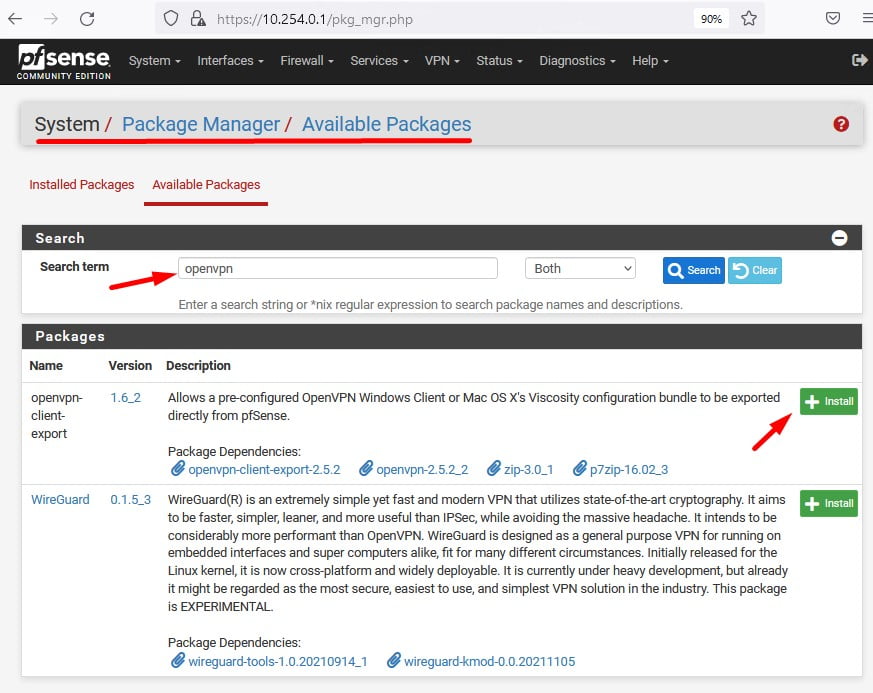
Atenção: Você precisa instalar uma unica vez este pacote, nas proximas vezes que for exportar as configurações do usuário basta navegar até a aba VPN em seguida clicar em OpenVPN e depois localizar OpenVPN Client Export.
Localize Client Export e desça a barra de rolagem até OpenVPN Clients, agora basta localizar o usuário e selecionar a versão do cliente que deseja instalar na estação de trabalho. Neste exemplo iremos utilizar a versão mais recente que é a 2.5.2 x64
Realizar a instalação do cliente (Basicamente next next finish…)
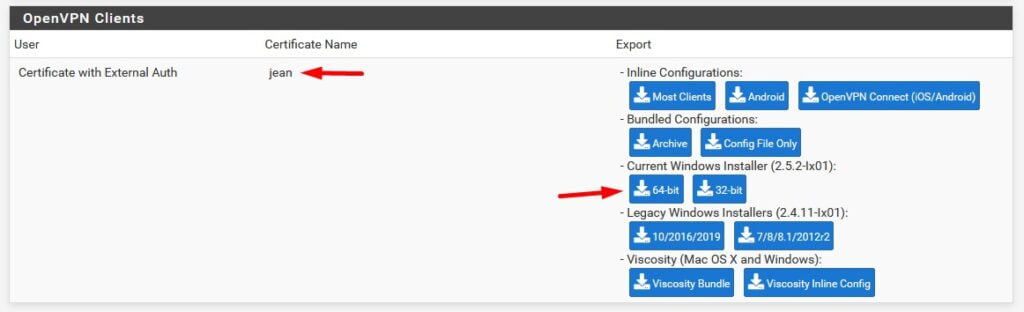
Após instalado basta procurar na bandeja do Windows próximo do relógio pelo OpenVPN GUI, selecionar a sua configuração e em seguida clicar em conectar.
Observe que no meu caso já estava conectado e nos prints a seguir você pode verificar a evidencia.
Obs: Esta nomenclatura pfSense-UDP4-11940-jean você pode facilmente modificar acessando o diretório C:\Program Files\OpenVPN\config selecionado o arquivo com .ovpn e renomear.
Após conectado na VPN através do usuário jean você pode observar que o IP da minha estação de trabalho no tunel da VPN é o 172.16.0.2 (CMD) já no Web Configurator adicione o Widget OpenVPN e observe o usuário e IP conectado.
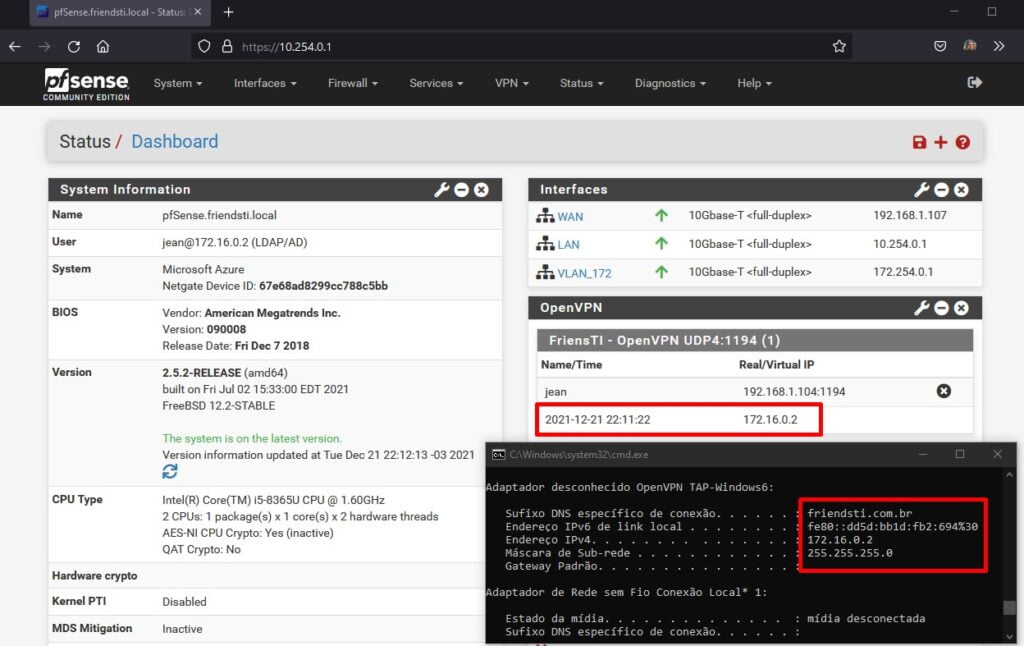
Lembrando que estes são IPs privados pois estou num ambiente de laboratório montado no Hyper-v em meu Laptop, para testes lembre-se de deixar bogon networks desabilitados pois caso contrário você pode ter problemas.
Neste tutorial aprendemos a integrar a nossa cliente VPN SSL que utilizar o OpenVPN com o nosso Active Directory, porem os usuários que fazem parte da OU configuradas lá no primeiro tutorial poderão acessar esta VPN caso alguém compartilhe o certificado e ou alguma pessoa mal intencionada queira utilizar a estação de trabalho de outro colaborador com as suas credencias.
Sendo assim num próximo tutorial irei abordar como podemos segregar estes acessos através dos grupos do Active Directory.
Referências:
Authenticating OpenVPN Users with RADIUS via Active Directory
Gostou? Curta e compartilhe!
Duvidas, críticas ou elogios deixe nos comentários!
Veja também:
TUTORIAL: COMO CRIAR NAT NO PFSENSE
DICA: PING EXTERNO NA WAN DO PFSENSE






Boa Tarde jean.
você já configurou para filtrar por grupo do ad?
estou tendo problema, pois ao ativar “Enable extended query” e inserir o grupo para realizar a autenticação, a liberação só ocorre com o usuário inserido na UO da opção “Authentication containers”.
simplesmente o “extended query” é ignorada.
estou utizando a versão 2.6.0
Boa noite!
Ja configurei sim!
Você seguiu o primeiro tutorial que fiz sobre a integração com o AD? https://friendsti.com.br/integracao-pfsense-com-active-directory/
Se sim observe a query que vc configurou esta mais ou menos deta forma: |(&(objectCategory=user)(memberOf=CN=G_ADM_OU=FriendsTI,DC=friendsti,DC=com,DC=br))(&(objectCategory=user)(memberOf=CN=G_VPN,OU=FriendsTI,DC=friendsti,DC=com,DC=br))
Observe que a Query, tem o grupo de ADM que são dos usuários administrador do pfSense e também o grupo G_VPN que são dos usuários de VPN apenas…